10 IT Asset Management Challenges and Fixes in 2026
Table of Contents
- Why IT Asset Management Still Matters in 2026?
- 10 IT Asset Management Challenges and How to Fix Them
- Incomplete Asset Inventory
- Shadow IT & Unauthorized Devices
- Inaccurate Lifecycle Tracking
- License Non-Compliance
- Poor Integration with Other Systems
- Lack of Real-Time Data
- Missed Security Patches or Updates
- Asset Loss or Theft in Remote Setups
- Inconsistent Asset Disposal Process
- Limited Visibility into Usage and ROI
- Asset Management Challenges, Risks And Solutions
- How Platforms Like ProHance Help Solve These Challenges?
- Final Thoughts
- FAQs
Work has fundamentally changed. The traditional asset management approaches don’t work anymore. Keeping track of IT assets is no longer a background task—it’s now central to how modern businesses run.
As organizations scale and shift to hybrid models, IT asset management challenges face a new wave of complexity. This guide breaks down the top 10 IT asset management problems companies are facing in 2026—and how IT asset management software can help address them with practical fixes that actually work.
Why IT Asset Management Still Matters in 2026?
These IT asset management risks aren’t theoretical problems for other companies – they’re happening right now:
- Compliance failures
- Cybersecurity breaches
- Operational inefficiencies
The asset management system market is gaining serious momentum. In 2026, it is valued at USD 17.64 billion—and it’s not slowing down anytime soon. Projections show the market could hit USD 26.41 billion by 2030, growing steadily at around 8.4% each year.
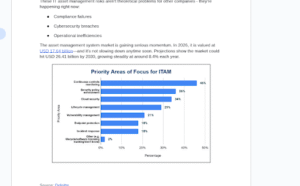
Source: Deloitte
10 IT Asset Management Challenges and How to Fix Them
Every organization encounters these same asset management problems.
- Incomplete Asset Inventory
- Shadow IT & Unauthorized Devices
- Inaccurate Lifecycle Tracking
- License Non-Compliance
- Poor Integration with Other Systems
- Lack of Real-Time Data
- Missed Security Patches or Updates
- Asset Loss or Theft in Remote Setups
- Inconsistent Asset Disposal Process
- Limited Visibility into Usage and ROI
Some acknowledge them openly, others pretend everything’s fine while quietly panicking.
1. Incomplete Asset Inventory
Challenge: Many organizations still operate without full visibility into all assets. Without real-time tracking, assets go missing, updates get delayed, and decisions take longer than they should.
Fix: Adopt centralized asset tracking tools with real-time updates. Integrate with service desks and usage analytics.
Modern discovery tools:
- Actively scan networks
- Identify connected devices
- Catalog installed software without human intervention.
Discovery tools work best when connected to help desk systems, procurement databases, and employee directories.
2. Shadow IT & Unauthorized Devices
Challenge: Employees working in a hybrid mode sometimes use devices or applications that remain unauthorized or untracked. Here’s what happens:
- Marketing teams subscribe to fancy design tools without mentioning it to IT.
- Sales people download CRM apps to their personal phones for “convenience.”
- Remote workers connect their home printers to the corporate network.
Fix: Introduce IT asset usage monitoring. Implement app/device authorization policies.
- Simple request forms can help your employees get legitimate tools quickly.
- Deploy monitoring tools that detect unauthorized activity without being invasive.
3. Inaccurate Lifecycle Tracking
Challenge: Poor tracking of purchase dates, warranties, upgrades, and end-of-life timelines.
Organizations that track asset lifecycles properly:
- Plan replacements
- Negotiate better support contracts
- Avoid the panic that comes with unexpected downtime.
Fix: Use automation tools to tag, categorize, and update asset status regularly.
Automated lifecycle tracking systems:
- Import purchase data directly from procurement systems
- Track warranty periods automatically
- Send alerts well before critical dates arrive.
Some advanced platforms even predict when assets will need replacement based on usage patterns and historical failure rates.
4. License Non-Compliance
Challenge: Overuse or underuse of licenses can lead to fines or unnecessary costs.
Software licensing has become more complicated than tax law. Overuse triggers compliance violations and surprise audit bills that can reach millions of dollars.
Fix: Use license management systems that sync with procurement and user data.
License management demands:
- Monthly reconciliation to catch problems early
- Automated tools to track usage patterns in real-time
5. Poor Integration with Other Systems
Challenge: The Asset management problems compound when systems can’t communicate and cause process gaps.
The result is predictable:
- Duplicate data entry
- Inconsistent information
- Missed opportunities for optimization.
Fix: Use platforms like ProHance that enable:
- Cross-platform visibility
- Integration with existing tools.
A unified view that makes decision-making faster and more accurate while reducing manual work.
6. Lack of Real-Time Data
Challenge: Static spreadsheets and manual logs delay decision-making.
Spreadsheets create dangerous delays between:
- When changes happen and
- When they appear in reports.
This delay becomes critical during emergencies.
Fix: Switch to cloud-based ITAM solutions like ProHance that deliver real-time dashboards and alerts.
- Real-time alerts showing what’s happening right now.
- Interactive dashboards provide instant visibility into trends, patterns, and anomalies.
The time saved on manual updates and emergency responses pays for the platform investment within months.
7. Missed Security Patches or Updates
Challenge: Unpatched systems increase vulnerability to cyberattacks.
- When devices leave secure office networks, they’re more likely to miss automated updates.
- Personal devices accessing corporate data add another layer of risk.
Fix: Automate patch tracking and compliance monitoring across all endpoints.
Patch management tools:
- Identify missing updates automatically
- Can install approved patches during scheduled maintenance windows.
8. Asset Loss or Theft in Remote Setups
Challenge: Remote or hybrid work increases the risk of losing physical or digital assets.
Each lost device represents:
- Replacement costs
- Productivity loss
- Potential data exposure.
Fix: Track assets by user, location, and activity using centralized monitoring tools.
- Asset tracking solutions monitor device locations, usage patterns, and security status continuously.
- Remote wipe capabilities protect sensitive data when devices are lost or stolen.
- Automated access controls revoke credentials based on employment status and project timelines.
9. Inconsistent Asset Disposal Process
Challenge: Improper decommissioning can create serious risks of data breaches or compliance violations.
- Improperly wiped drives expose confidential customer information years later.
- Improper disposal methods violate environmental regulations and create potential liability.
Fix: Create standardized disposal protocols, including data wiping and certificate-based destruction tracking.
Formal disposal procedures ensure:
- Consistent data destruction
- Proper recycling.
10. Limited Visibility into Usage and ROI
Challenge: Companies often lack insight into how assets contribute to productivity or value.
The lack of visibility leads to:
- Purchasing unnecessary equipment
- Overlooking opportunities for cost savings.
Fix: Use workforce analytics to track usage patterns and correlate asset usage with business outcomes.
Analytics platforms reveal which assets provide genuine value and which just drain your budget.
Asset Management Challenges, Risks And Solutions
| Challenge | Primary Risk | Solution Type |
| Incomplete Inventory | Security blind spots | Automated discovery |
| Shadow IT | Compliance violations | Usage monitoring |
| Lifecycle Tracking | Budget surprises | Automation tools |
| License Non-Compliance | Audit failures | Regular reconciliation |
| Poor Integration | Process inefficiencies | Unified platforms |
| Outdated Data | Delayed decisions | Real-time dashboards |
| Missed Patches | Security vulnerabilities | Automated updates |
| Asset Loss | Data breaches | Remote monitoring |
| Disposal Issues | Compliance violations | Standardized processes |
| Limited ROI Visibility | Wasted investments | Usage analytics |
How Platforms Like ProHance Help Solve These Challenges?
ProHance provides essential capabilities that solve common problems:
- Real-time asset tracking dashboards – Live visibility into asset status, location, and performance metrics.
- License and compliance monitoring – Automated tracking of software usage against entitlements with instant alerts.
- Integration with workforce performance metrics – Direct connection between asset usage and productivity outcomes for accurate ROI measurement
- Alerts for underutilized or risky assets – Proactive notifications about optimization opportunities and security risks.


https://www.flexera.com/blog/it-asset-management/itam-trends-and-insights-2024-state-of-itam-report/
Final Thoughts
Addressing these common IT asset management challenges directly impacts security, cost control, compliance, and overall efficiency. Companies that invest in smart ITAM will be better positioned to adapt to developing business needs and technology landscapes.
The challenges are real and growing, but practical solutions exist. The question isn’t whether to improve asset management practices – it’s how quickly meaningful improvements can be implemented and sustained.
FAQs
What are the biggest IT asset management risks in 2026?
The most significant risks include:
- security breaches from unmonitored assets,
- compliance violations from inadequate license tracking, and
- operational inefficiencies from incomplete visibility.
Is cloud asset management included in ITAM?
Yes. Cloud resources, virtual machines, and SaaS tools all fall under modern ITAM. Tracking usage, spend, and renewals for these assets is now standard.
How can organizations effectively address shadow IT?
Organizations can handle Shadow IT through the following approaches:
- Deploy usage monitoring tools,
- Establish streamlined approval processes, and
- Educate employees about security risks.



